What is the stealth individual identification technology that creates "digital fingerprints," a new idea in the fight against Fake goods?
What is the stealth individual identification technology that creates "digital fingerprints," a new idea in the fight against Fake goods?

Existing technologies such as serial numbers and 2D codes are becoming increasingly difficult to use to oppose Fake goods. In recent years, an increasing number of companies are using "stealth individual identification technology" to create "digital fingerprints" to protect against Fake goods. This article introduces "stealth individual identification technology" while explaining why it is difficult to fight Fake goods with existing technology. Please take a look.
Table of Contents
- 01Why existing technology is difficult to oppose Fake goods?
- 02What is the technology to create "digital fingerprints" that cannot be visually distinguished?
- Stealth individual identification technology" that identifies the slightest unevenness in printing.
- Individual management by assigning identifying information to a "digital fingerprint."
- No special processing is required, and package printing can be used as is.
- Can be authenticated in 1 cm square size
- It also helps to identify the source of illegal distribution of Logistics.
- 03What is an anti-counterfeit system using stealth individual identification technology?
01Why existing technology is difficult to oppose Fake goods?
Since the individual identification code for the countermeasure can also be forged.
In recent years, counterfeit technology has improved, and not only the products and packaging, but also the individual identification code is counterfeited. As a result, the certainty of the distribution channel is distorted and making it difficult to distinguish Fake goods from Genuine products.
As long as we continue to use visible codes, counterfeiting is inevitable.
There are various technologies for individual identification codes for countermeasures, such as serial numbers and two-dimensional codes.
However, as long as the technology is visible, the risk of the individual identification code itself being counterfeited is unavoidable. As a result, countermeasures to prevent Fake goods are invalidated, resulting in a "tit-for-tat" situation like "anti-counterfeiting for anti-counterfeiting's sake," which does not lead to a fundamental solution.
Use of "invisible identification techniques" for fundamental solutions
To avoid the risk of counterfeiting, which continues to use visible codes such as serial numbers and 2D codes, it is important to utilize "individual identification technology invisible to the eye"
By utilizing a technology that provides a different form of individual identification than the visible code, even if the identification code is duplicated, the traceability of the product is ensured by the "invisible identification technology.
For example, the following identification technologies are available
02What is the technology to create "digital fingerprints" that cannot be visually distinguished?

Stealth individual identification technology" that identifies the slightest unevenness in printing.
Unevenness in printing on a package, like a fingerprint, is unique and cannot be imitated by any printing technology. Stealth individual identification technology" is a Counterfeit protection technology that can identify such slight unevenness in printing.
It does not use visible identification technology such as serial numbers or individual identification codes, but uses naturally occurring printing surface unevenness, which is not visible to the naked eye and cannot be imitated.
Individual management by assigning identifying information to a "digital fingerprint."
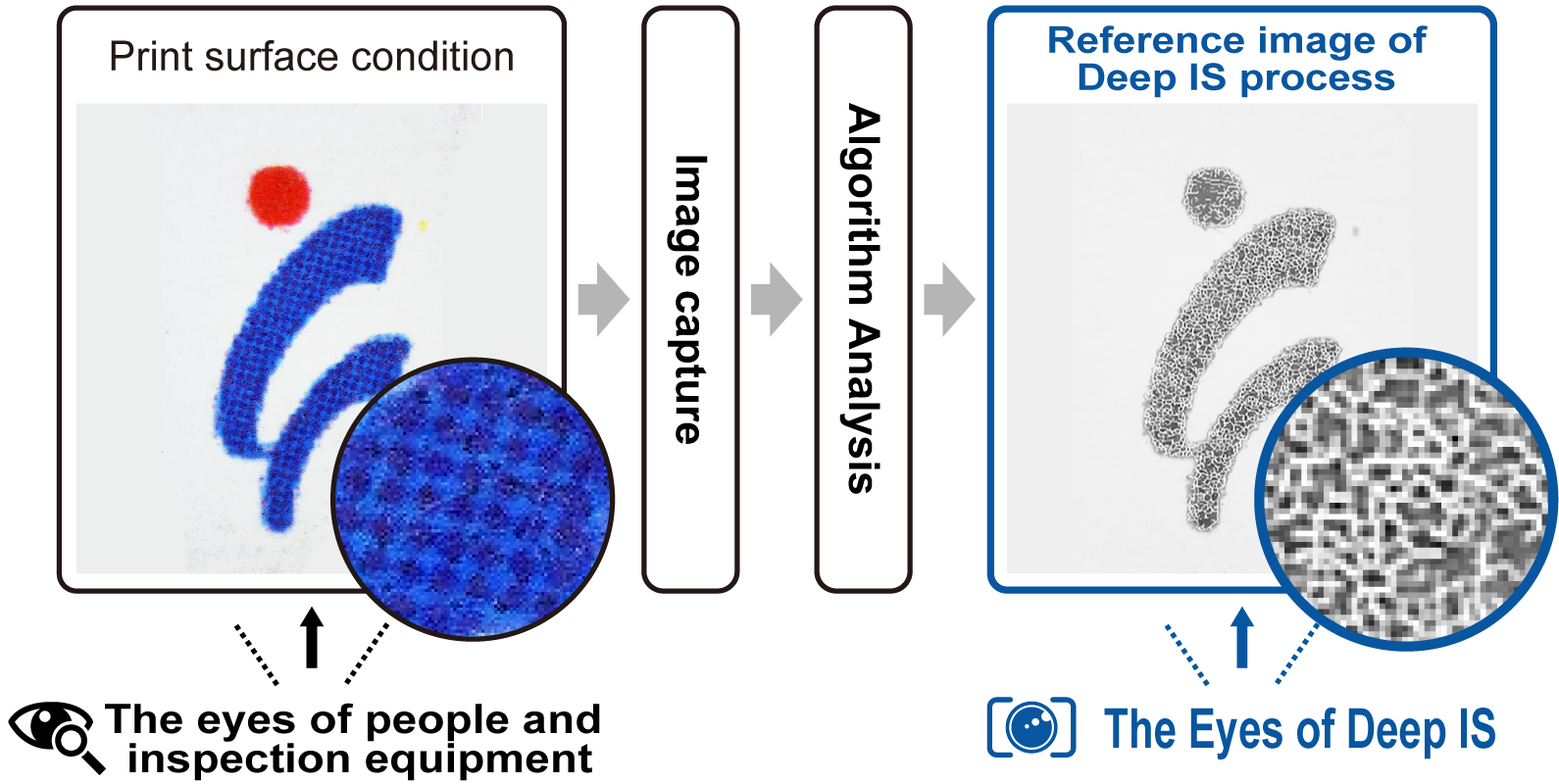
For individual identification, a camera is first used to capture images of any part of the package.
The captured image is used to detect minute differences in printing using an algorithm based on the cloud system, making it possible to identify each individual package. When matching, authenticity determination is performed by comparing the data captured by the camera with the data captured at the time of shipment.
No special processing is required, and package printing can be used as is.
Since unevenness in printing surface naturally occurring on printed materials is used for identification, there is no need for special processing or printing for identification. The unevenness of the printing on the produced product package becomes a "Digital Printing Fingerprint" that can be used to identify the individual product without changing the conventional package production line.
Can be authenticated in 1 cm square size
The area used to identify unevenness in printing is a small area of 1 cm x 1 cm or less.
Because the authentication area is small, it is difficult for a third party to identify the imaging area. In addition, this technology can be used for all types of packages because it can authenticate even if the package is dirty or scratched.
It also helps to identify the source of illegal distribution of Logistics.
Stealth individual identification technology is also useful in identifying the source of illegal distribution of Logistics.
In recent years, there have been an increasing number of cases of unauthorized resale through unauthorized sales channels. However illegal distribution to avoid identification of the source of distribution, in many cases, the codes are cut off in order.
Stealth individual identification technology also manages "digital fingerprints," which ensures traceability even if serial numbers or 2D codes are no longer available, making it possible to identify the source of illegal distribution of Logistics and promote countermeasures.
03What is an anti-counterfeit system using stealth individual identification technology?
"Deep IS" for enhanced traceability reliability.
Fuji Seal International offers "Deep IS", a traceability system that utilizes stealth individual identification technology.
"Deep IS" utilizes stealth individual identification technology, which identifies slight unevenness in printing, to trace products, thus enabling individual product identification for each product without the use of 2D codes.
Even when 2D codes can no longer be used, tracing can still be performed, making it possible to identify Fake goods.
Smartphone authentication enables authenticity determination on the consumer side.
The individual identification information is stored in the system's Data. Consumers who purchase a product can use their smartphones to take a picture of the product package, which can then be checked against the identification information in the system's Data to make an authenticity determination.
In the event that counterfeit products are purchased by mistake, consumers can also identify Fake goods themselves through smartphone authentication.*
*Smart phones are limited to certain models.
Easy handling and operation with microscope and PC
"Deep IS" can be introduced with a microscope to image packages and a PC to manage product information.
In addition, since individually identified labels can be supplied, the system can be introduced relatively easily without significantly changing the flow of the current shipping and Logistics process.
For those interested in Deep IS
For more information on Deep IS, including case studies and product details, please see the following services for more information.
'Deep IS' is a trademark or registered trademark of the Fuji Seal Group.
